Application Case of GNS-1304 in Power Monitoring Audit
The power industry is the fundamental industry of the national economy, and its safety is directly related to people's livelihoods.
With the continuous development of smart grid construction, how to avoid security risks such as sensitive internal and external information leakage, malicious and irregular operations, and how to ensure database security have become the focus of information security construction in the power industry.
Requirement analysis:
According to the threat and risk analysis of the database system for the comprehensive power business, data center, and power trading in a certain province, the database security audit requirements of the unit mainly focus on the following aspects:
Comprehensive monitoring of various account access operations
Real time monitoring of operational behavior, timely alerting and responding to illegal and irregular operations discovered
Detailed record of database operation information, and provide rich audit information query methods and reports to facilitate security incident location and analysis, as well as post event investigation and evidence collection
The construction of information security in the power system must meet the requirements of relevant regulations and level protection
Solution for Monitoring and Auditing Power Network Security
The design and construction principles of this solution are mainly based on the system construction requirements of Equal Protection 2.0 and relevant specifications for information security in the power industry.
By deploying a professional security audit system in the construction network, database access behavior can be effectively monitored, the security status of the database system can be accurately grasped, and incidents that violate database security policies can be detected in a timely manner and alerted and recorded in real time. At the same time, security incident location analysis can be carried out, and evidence collection can be conducted afterwards to ensure the security of the unit's database.
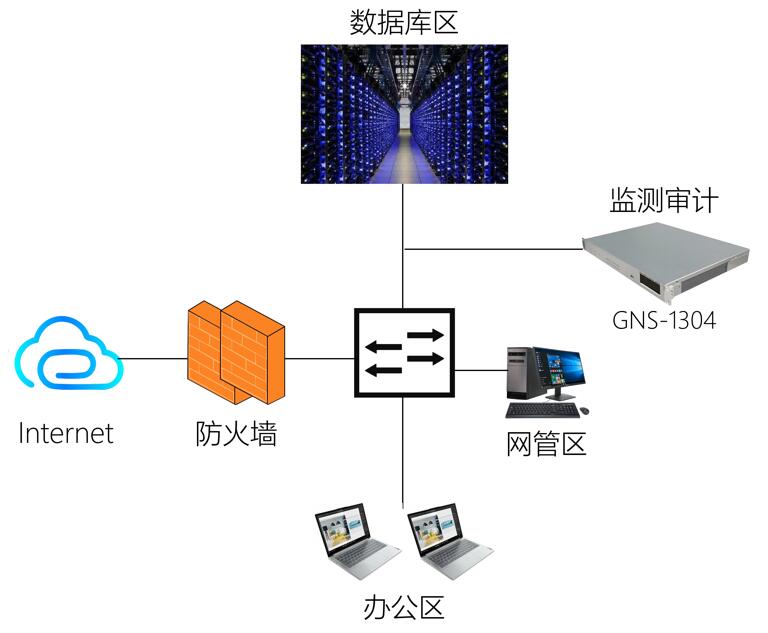
Strengthened monitoring and auditing of all accounts
Strengthened audit monitoring for access to important sensitive data
Provided detailed audit records and classified statistics
Implemented abnormal operation monitoring and alarm
Compensated for the deficiency of built-in log auditing in the system
The hardware of the monitoring and auditing system adopts the GNS-1304 industrial computer, a fanless power monitoring system network security monitoring device developed by Jizhida.

Strengthened monitoring and auditing of all accounts
Strengthened audit monitoring for access to important sensitive data
Provided detailed audit records and classified statistics
Implemented abnormal operation monitoring and alarm
Compensated for the deficiency of built-in log auditing in the system